In this post, I will share my thoughts on the recent PR disaster surrounding Ledger, a leading crypto hardware wallet provider. As an avid user of their Ledger Nano X, I had previously praised their security features. However, with the introduction of their controversial “Ledger Recover” service, the company has faced significant backlash from the community. Let’s delve into the details and explore the implications.
The Inaccurate Claim and Online Backup
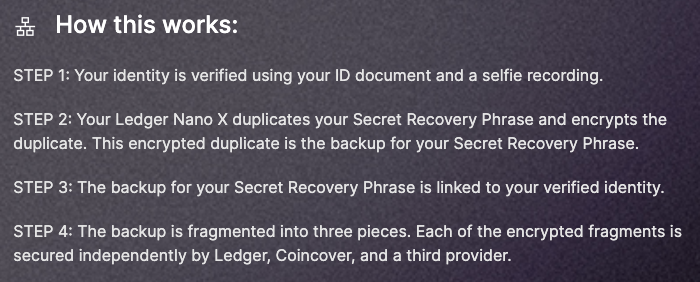
In a previous post, I highlighted the importance of hardware wallets in safeguarding private keys. However, it has come to light that Ledger’s new service involves encrypting private keys, splitting them into three parts, and entrusting them to separate companies. While a single part is useless alone, only two parts are needed to recover the private keys. This contradicts my earlier claim that private keys never leave the device. Ledger argues that this service is optional and performed on their hardware, but the community remains concerned.
Loss of Trust and Competitor Advantage
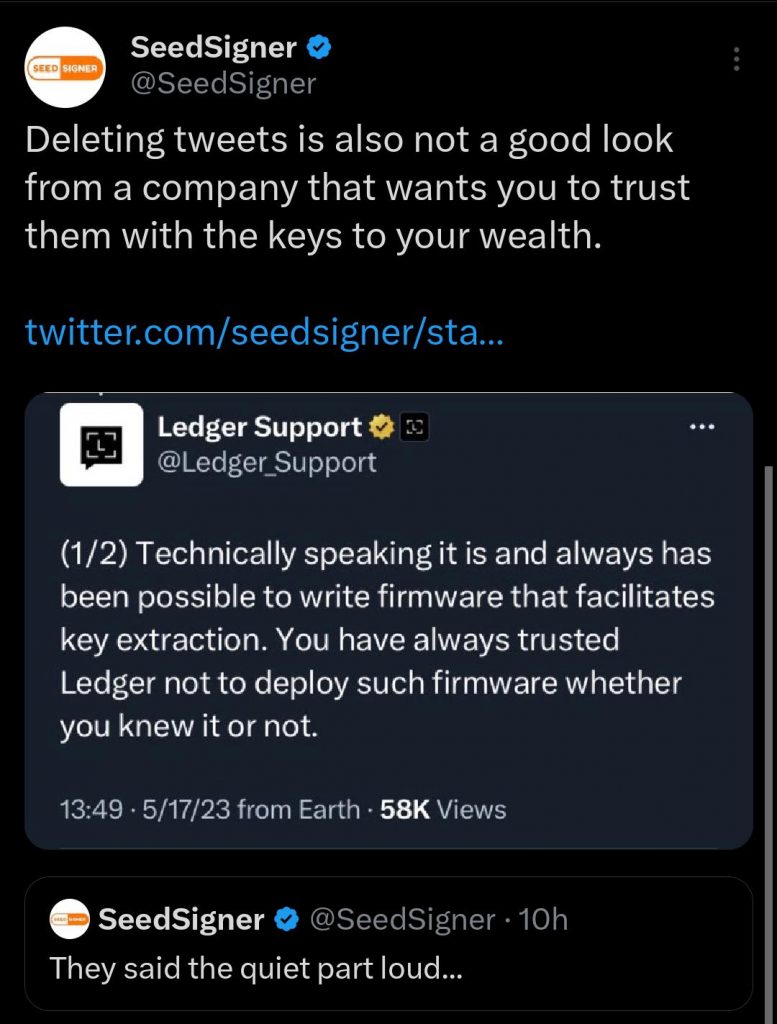
Ledger’s wallets were known for their strong security measures and the assurance that once keys were created, they couldn’t be extracted from the device. Many users made purchasing decisions based on this promise, leading to a significant customer base. However, this PR disaster has eroded trust, prompting users to consider alternatives and switch to Ledger’s competitors for their hardware wallet needs. Adding fuel to the fire, a now-deleted tweet from Ledger support claimed that private key extraction had always been possible with a firmware update.
Assessing the Reaction and Trustworthiness
Éric Larchevêque, a co-founder and former CEO of Ledger, acknowledged the gravity of the situation, labelling it a PR disaster. He emphasized that all hardware wallets rely on trust in the manufacturer. While I agree with Éric’s perspective, Ledger’s previous mishandling of customer data breaches raises concerns. With some customers still experiencing targeted phishing attacks from the breach, I am hesitant to subscribe to the Ledger Recover service. Instead, I prioritise the safety of my seed words. Nevertheless, Ledger’s hardware itself has not been proven vulnerable to hacking, unlike its competitor Trezor.
Open Source vs. Closed System
One drawback of Ledger’s system compared to Trezor is its closed-source nature. Trezor’s platform is open source, allowing for independent audits and verification by the community. Many members of the Ledger subreddit are demanding that Ledger open their hardware’s firmware source code to rebuild trust. Transparency and accountability in the form of open-source practices might be crucial for users to regain confidence in Ledger’s devices.
Conclusion
While the situation is still unfolding, Ledger’s actions will be pivotal for the company’s survival in the coming weeks. As of now, I cautiously recommend Ledger to new users. However, I advise against enrolling in the Ledger Recover service and suggest waiting a few weeks to assess how the company handles this significant PR crisis. Stay informed and make informed decisions to ensure the security of your crypto assets.
Cheers













