Just over 15 years ago I used to watch a television programme on the BBC called Tomorrow’s World, the show focused on new and emerging technologies which could end up in our everyday lives. Famously, the humble Compact Disc was featured, and to this day, they’re still one of the standard methods of legally distributing music. Something from the show that caught my attention was a new piece of software which allowed the transfer of computer data via the medium of paper.
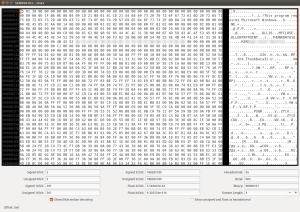
The technology was named Intacta.CODE by Intacta Technologies, Inc. of Atlanta, GA, USA. What it could do was to accept files on your computer, and print it out as a 2D barcode (similar to QR code) which could later be scanned back in and the original files recovered. Tomorrow’s World presenters Peter Snow and Phillipa Forrester demonstrated how it worked, which also featured a demonstration of Intacta’s error correction system, shown by Peter printing out a code containing a document, stabbing holes through it, crumpling it up and throwing it across the room to Phillipa, who then proceed to scan the file in and successfully recover the document. At the time that episode of Tomorrow’s World went to air on 17th May 2000, Intacta was offering a free utility to read code, the idea was to allow publishers (such as newspapers) to use Intacta.CODE to embed files into their printed publications (The program was called “Color Scan & Fax Read”). Previously (according to web archive) it was also possible to download Intacta Express which would let you create code and lets you either print the output, save to file, email to another user, or even fax the result.
The technology didn’t really take off, with Intacta repurposing their business model to focus on the healthcare sector, allowing patient information to be stored securely offline with Intacta.CODE.
Mean while, in Japan, Intacta.CODE had already had some success, where an application to decode the barcodes came preinstalled on some PCs manufactured by Fujitsu. I found a copy of this in the deep dark corners of the Internet Archive’s Wayback Machine along with some Intacta.CODE examples. I wanted to show this off for a school project, so I used Resource Hacker and online translation software to modify the application to have its dialogs in English, I also rewrote the documentation for using it, and submitted it as part of my project.
One thing I noticed about the Japanese application was that it couldn’t decode any of the examples I had downloaded from the Intacta website back in the year 2000. A former employee of Intacta contacted me in 2011 and confirmed the Japanese version couldn’t decode those files and gave me the following reason:
The reason that one program can’t read code created by other program
is basically technical. It is all to do with the way the barcode is
created and the “seed” of the random code that creates the barcode.
Another reason could be that different clients/programs are assigned
to one code while other to other code.This obviously is controlled by the program that creates the code. The
reader must “know” this information.Basically, it is possible to create universal writer and universal reader.
In late September 2009, I was contacted by someone who happened to find the Intacta.CODE reader which had been downloaded from Intacta’s website. They also sent me a copy of Intacta Express which was also available to download at the time. I immediately put the reader software on the unofficial Intacta.CODE site, but as for Intacta Express, there was a small issue, which brings me onto the actual topic of this post.
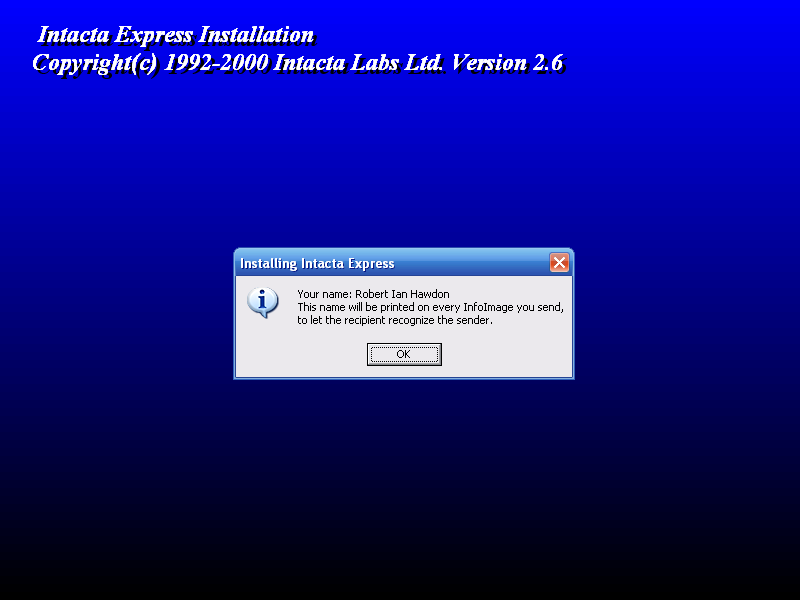
Upon installation, it automatically fills in the original user’s name, this name is then baked into all codes generated. After consulting the person who donated the software to me, we agreed that it shouldn’t be made public whilst their name was still coded into the program.
I grepped all the files in the installation folder to see if the name appeared in plain text which resulted in a match found in the binary file “SENDER.DLL”.
Opening up the file in a Hex editor, I tried the obvious things, replacing the name with null characters, deleting the name, even replacing it. Each time, the installer would fail to load saying the SENDER.DLL file was corrupt. Clearly further work was required. At this point I shelved the software.
Every couple of years I’d have another look, but trying to find resources on the Internet about getting around this user lock was almost as impossible as finding information about Intacta.CODE itself.
This week, I decided to give reverse engineering another shot. I grepped for “SENDER.DLL” in the installation files. This gave the result that it was being referenced in plain text in the TLINST.DLL file. The description of this file was “Extentions for 3D FaxFile English Pro”, this was a little set back as it was a custom made DLL for Infoimaging’s 3D FaxFile, the software Intacta was basing their software on. Now I’m not totally sure about Intacta’s link to Infoimaging was, but from some research, it looks like they went out of business in 2001, whilst Intacta seemed to still be in business until 2004.
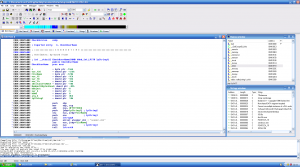
So the next logical step was to investigate the TLISNT.DLL file a bit more closely, so I used IDA Pro (By Hex-Rays) to disassemble the file into assembly code. Now assembly isn’t my strong point, but I was able to get a better grasp of what this file was doing with the SENDER.DLL file.
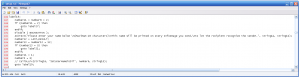
In this file, there were two functions that referenced the SENDER.DLL file, one called CheckUserName and another called SetUserNameToDLL. From this my initial thought was to see how to force the installation to use the SetUserNameToDLL file. So I went about looking for a way to disassemble the installer. It turns out the installer was InstallShield version 3, and that a tool had been created to disassemble the installer script in to a semi readable, but crucially, a re-compilable rules file.
The issue is that the disassembler can’t recover the original label names, so following this script through took some time. It turned out that it seemed that the SENDER.DLL file was used purely to set the name during install time, and that there was a dialogue box scripted to allow for the user to set a name to be used, presumably to use the “SetUserNameToDll” function in the TLINST.DLL file, but it was not implemented in any way leading to dead ends in the rules file. I did initially try to use that function to change the name in the SENDER.DLL file, but it didn’t seem to be fully implemented in the TLINST.DLL file either and the file remained unchanged. But looking further in the script, it seemed that the name pulled out of the file was passed in plain text to the rest of the installation. So, I eventually rewrote the initial part of the script to ignore the SENDER.DLL file and show the unused dialogue box to input the user’s name instead, and to take the output from that and use it for the rest of the installation.
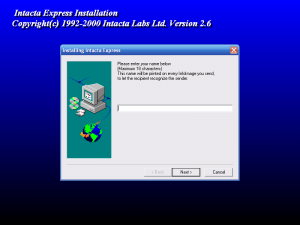
The final issue was to track down a copy of InstallShield 3 to recompile the rule file, and then to add that back to the installation. Once I found it, I was able to give the installation another shot. I completely removed the SENDER.DLL file for this test.
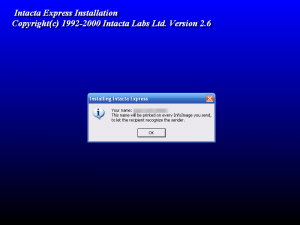
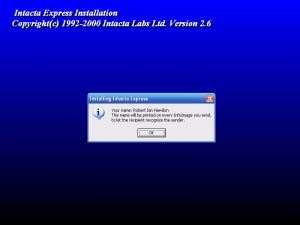
This time, we’re greeted with a prompt asking for a name.
This time, the installer confirms that my name will be used in the program. Lets finish the installation and test it out.
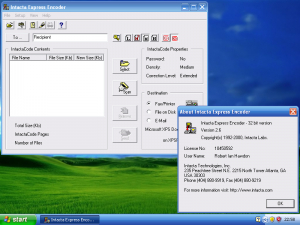
Finally, looking at the program itself, it shows my name in the about section, and will encode my name on to every Intacta Code generated.
I can now, after 6 years, happily announce the general availability of Intacta Express – Version 2.6 for download at my Intacta Code site. As the company no longer exists, I consider this software abandonware, and should be available for historical purposes.
Side Note: It’s important to note that the InstallShield 3 installer uses a 16-bit launcher. This will cause problems when attempting to install on 64-bit Operating Systems (Hence the heavy use of Windows XP in this post). There are guides on the internet that help allow you to install InstallShield 3 wrapped installers on 64-bit systems. The program itself is 32-bit, so there shouldn’t be any issues running it on modern systems when it is installed.
I also can’t be held responsible for any data loss as a result of using this software.
I will eventually try and get round to wrapping this software up into a portable version, but that’s not going to happen for a while I expect.
For those who have installed it, download the example near the beginning of this post and see if you can decode it. Don’t worry, it’s only a picture of yours truly. 🙂
Cheers